
How often should you service your air conditioning?
Maintaining your air conditioning system is not only a matter of comfort but also a pivotal component of energy efficiency and prolonged equipment life. The question that frequently arises is, how often should you service your air conditioning unit, and what drives this necessity? Service Frequency: Striking the Right Balance The general consensus among companies…
Read More
What to look for in IT Support Companies
In the ever-evolving realm of business operations, Information Technology (IT) support has emerged as a crucial element for companies seeking to stay ahead in an increasingly digital world. Many businesses, both large and small, are recognizing the value of specialized IT expertise to handle tasks ranging from system implementation to troubleshooting and repairing server and…
Read More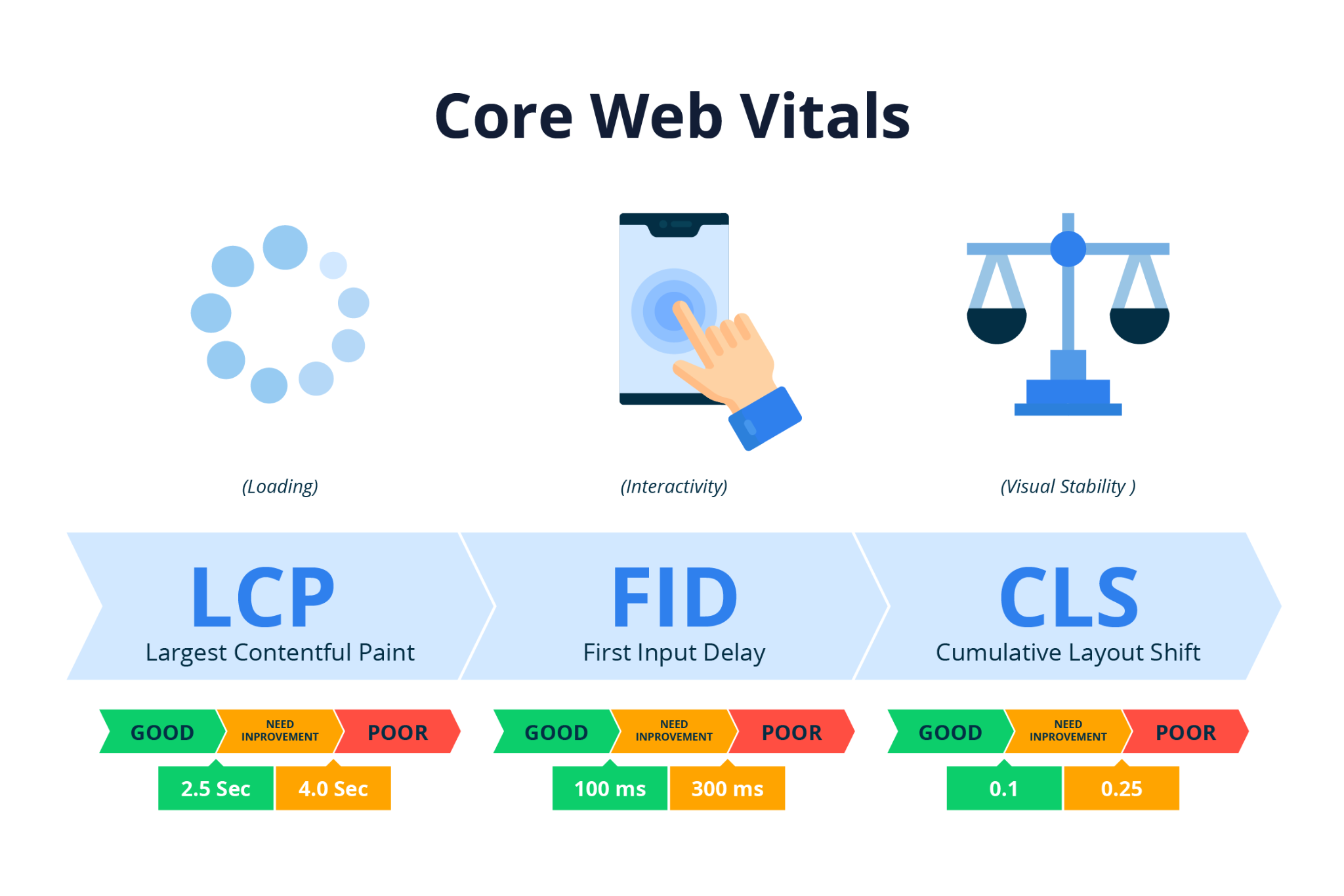
What Are Core Web Vitals?
Article by Pierre Zarokian. Core Web Vitals are a set of specific factors that Google considers crucial in assessing the overall user experience on a website. Introduced as part of Google’s Page Experience update, Core Web Vitals focus on key aspects of web page loading, interactivity, and visual stability. These metrics aim to help website…
Read More
What is the difference between a laptop and a Chromebook?
In the ever-evolving landscape of personal computing, choosing the right device can be a daunting task. Laptops and Chromebooks stand out as two prominent contenders, each with its unique set of features and functionalities. Understanding the differences between these devices is crucial for making an informed decision that aligns with your needs and preferences. Performance…
Read More
How to write SEO content using AI?
Article by Pierre Zarokian. In the dynamic landscape of digital communication, online marketing has become an indispensable tool for businesses to connect with their target audience. Content marketing plays a pivotal role in this strategy, making it imperative to consider factors such as search engine optimization (SEO) for content success. The growing popularity of SEO…
Read More
Leerink Partners: The Story of One of Boston’s Prominent Investment Banks
Leerink Partners stands as a prominent name among financial institutions in Boston, particularly in the healthcare sector. Established in 1995 as Leerink Swann by Jeffrey A. Leerink, the independent investment bank has undergone significant transformations over its nearly three-decade journey. Today, it is renowned for offering a diverse range of financial services to healthcare companies,…
Read More
How to Effectively Game on an Apple Computer
Article submitted by Angelina Z. Summary: Gone are the days when gaming on a Mac was unheard of. Below are a couple of reliable methods to effectively game on a Mac today. Apple computers have had a bad reputation as being less than ideal for gaming purposes. Apple’s laptops and desktops are fast and reliable…
Read More
Keeping Your Equipment in Solid Condition
Summary: Keeping your equipment in good condition can help your office cut down on replacement expenses in the long run. Despite there being numerous ways you grow the business and work more efficiently, there are some incredibly simple ways you can help keep expenses low. For example, something as simple as equipment maintenance can help…
Read More
3 Ways to Browse Safely With Firefox
Is Firefox the most secure browser to use over the internet? At least, a majority of users believe so but that depends on the settings – a few of them have to be manually enabled. So, here are 3 ways to browse safely with Firefox: #1: Use the master password option Unlike Google Chrome, Firefox…
Read More
How Mobile 4G Internet Has Given Rural Residents More Shopping Opportunities
If you live in rural America, you may be used to having more limited opportunities to buy clothing, household goods, electronics, and other popular items people often shop for in the 21st century. However, with the advent of the Internet, people have been able to purchase assorted goods and merchandise from almost anywhere in the…
Read More